System updates go hand in hand with computers, even server computers. But some updates can change functionally, how machines communicate or interact with third party software.
Tag: Security

Danish Navy Sails into the Future with Thin Client Technology
After 15 years of active service, the Danish Navy needed to re-fit and modernize technology aboard the Absalon-class support ship. Logimatic and ThinManager make it happen.
VIDEO: ThinManager 10 » New Features
ThinManager 10 is full of new features to make life easier from the administrator to the end user. This version puts a focus on security and productivity and we are ready to tell about some of these exciting new features. Let’s take a look at what’s new.
Authentication Passthrough (productivity)
A successful login into a ThinManager terminal will now pass a security token into FactoryTalk Security, and any running session(s) of FactoryTalk View SE on that terminal will automatically take that security token to log in the associated user. For instance, if you have multiple sessions being delivered to a terminal in a control room environment, this will dramatically simplify the login process.
Previously, a user would have to manually login to each session of View SE—now this is done one time using a Relevance User in ThinManager. This feature improves both Security and Productivity.
WinTMC updated (productivity)
The new WinTMC client adds support for Virtual Screens, Tiling and IP Cameras – this will make WinTMC the first of our mobile clients to support these features. This allows users of a mobile Windows 10 device to maintain a control room view while on the move.
Password Caching and PIN Authentication (security)
Users can now use Password Caching to simplify mobility with in their work shift. A password authentication at the beginning of their shift will be cached to allow the user to move from terminal to terminal with only a simple badge scan, thumb scan or entered PIN without having to re-enter a password. The cache time out is set by the ThinManager administrator.
uTMC and Hololens (visualization)
ThinManager now supports the Microsoft Hololens with the uTMC client application. With added support for QR Codes, Bluetooth Beacons and Location Based content delivery; the support of the Hololens is now a reality and a truly ground breaking way to deliver essential content while keeping hands free to work was needed.
Resolvers (mobility)
With ThinManager 10, bluetooth enabled devices can now be used as a beacon for authentication. In addition, Version 10 leverages technology from Cisco’s HyperLocation with wifi and BeaconPoint with bluetooth to greatly improve indoor location resolving.
These are just some of the features that make ThinManager 10 the essential piece to the Connected Enterprise and today’s modern production environment. ThinManager 10 continues to build on the ThinManager Platform, the world leader in thin client management & industrial mobility solutions.
VIDEO: ThinManager 9 » New Features
Learn about all the new features in the latest release of ThinManager. We talk about Single Port TFTP, Terminal Server Grouping, Authenticated Email, SMS Messaging, USB Cameras, Virtual Screens, VNC Support and much more!

It’s in to be thin
ThinManager was mentioned in a recent LinkedIn Post from InSource Solutions about how thin client technology is more manageable, scalable and mobile.
Below are excerpts written by Jason Paquette, Product Marketing Manager at InSource Solutions, from his post regarding thin client management and mobility with an HMI.

Happy Manufacturing Day
As a “tip of the cap” to all those in this great industry, we have put together a video about ThinManager in a sit down interview with ACP’s CEO, Matt Crandell, asking where it all started, and where it is going. ThinManager is the global leader in thin client management and industrial mobility. Without our partners and customers in the manufacturing industry, we simply would not be where we are today.
To download and try ThinManager free for 30 days, please click the link below. Thank you to all that support us and the manufacturing industry. Happy Manufacturing Day!
[hs_action]

Using ThinManager – Location Resolver Technology
Location resolvers in Relevance are used to define locations throughout your plant. Examples of defined locations can be as broad as the entire network, a tethered thin client terminal, or a defined “geo-fenced” area. Relevance uses technologies such as Bluetooth, WiFi, GPS, NFC and QR Codes to let administrators define an unlimited number of locations.
With your locations defined, you can now deliver applications and content based on location to any number of modern mobile devices such as tablets and smart phones.
- Transfer – An authenticated user on a mobile device can transfer the content from a tethered terminal to their mobile device. When finished they can return it or have it return if the user leaves the “geo-fenced” location defined by the ThinManager Administrator.
- Clone – An authenticated user with high level or “Supervisor” access can receive content on their tablet cloned from each line as they pass between defined locations allowing them to easily monitor statuses and reports as they supervise.

Using ThinManager – Safety and Security
This video focuses on the security and data safety in ThinManager. ThinManager gives you complete control in your production environment over who sees what, where and when. Secure data management has always been in the forefront when creating ThinManager. Our location-based resolvers create “Geo-Fences” for total security when integrating mobility in to your production environment.
The Factory of the future runs on ThinManager. Start a free trial of ThinManager today.
[hs_action]

User Authentication with ThinManager
In a modern factory or production environment using ThinManager, there are several options at your disposal to make user authentication fast and amazingly safe and secure. ThinManager syncs with your existing Windows network Active Directory to provide an easy entry to your users and user authentication.
=&0=& – The tried and true method to proof of identity. ThinManager allows for keyboard incorporation giving users the ability to provide their network credentials and access the information you determine, at a terminal in which you have granted them the permission.
=&1=& – Faster than the traditional username and password, badge readers allow for the swipe or tap of a card badge, or insert of a smart card, to prove the identity of that user. Handy for touchscreen terminals where a keyboard might not be optimal. Card readers can also be used in part with a password for even more security. ThinManager now supports NLA (Network Level Authentication) policies depending on the configuration and desired method of use.
=&2=& – The newest module to ThinManger, finger print scanners add a unique level of security that can not be lost or forgotten by the user. Truly unique to each user, a fingerprint scanner allows quick proof of identity and is easily incorporated with ThinManager version 8 and higher.
Each method has pros and cons to their implementation and use, but ThinManager allows for each one in an effort to be flexible and incorporate with your business practices and company policies.
We all know that data security starts with user authentication. ThinManager remains the front runner in supporting secure methods for your users to show proof of identity.

Build The Ultimate Control Room
In today’s modern production environment visualization is not only important, it is essential.
Visualization is one of the cornerstones of ThinManager and building your ultimate control room to see everything in your production environment is simply put… “A Piece of Cake”!
Start by obtaining a capable thin client, one that can support multiple monitors. We like a configuration for at least 4 large monitors. Need suggestions, look at the ThinManager Knowledge Base of ThinManager ready hardware. Install and layout your monitors.
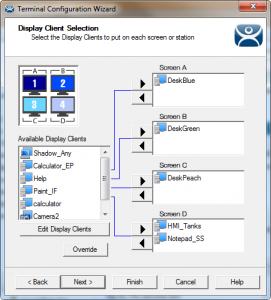 Using ThinManager you can now assign your control room thin client with all the applications, HMIs, IP Camera Feeds and Desktops that you will need to operate in complete control with optimal visualization of what is happening in your production environment.
Using ThinManager you can now assign your control room thin client with all the applications, HMIs, IP Camera Feeds and Desktops that you will need to operate in complete control with optimal visualization of what is happening in your production environment.
Quickly and easily “Shadow” plant floor terminals or take control if needed. You have options for “Tiling” on each individual monitor, as well as using camera overlays for even more visualization. You can ever move content from screen to screen on the fly!
Simply restart your control room terminal and you now have the set up you always wanted. It is just that easy and all simply built in to the functionality of ThinManager.
[hs_action]
